Leveraging Blockchain for Secure and Transparent Digital Identity Management
Leveraging Blockchain for Secure and Transparent Digital Identity Management – Do you want to know more about Leveraging Blockchain for Secure and Transparent Digital Identity Management? Then, this article is a must-read for you.
Yes; in an increasingly digitized world of ours, the need for secure and transparent digital identity management has become paramount. Traditional identity management systems often suffer from vulnerabilities, such as data breaches and identity theft, which compromise user privacy and security. However, the emergence of blockchain technology has opened up new possibilities for addressing these challenges. By leveraging the inherent features of blockchain, including decentralization, immutability, and cryptographic security, organizations can revolutionize digital identity management, ensuring trust, privacy, and transparency for individuals and entities alike. This article; Leveraging Blockchain for Secure and Transparent Digital Identity Management, explores how blockchain can be harnessed to create a robust and reliable framework for secure and transparent digital identity management.
Contents
- 1 Why Mus you Read This Article?
- 1.1 Enhanced Security:
- 1.2 Improved Privacy:
- 1.3 Transparency and Trust:
- 1.4 Simplified Identity Verification:
- 1.5 Potential for Self-Sovereign Identity:
- 1.6 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.7 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.8 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.9 Further Facts:
- 1.9.1 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.9.2 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.9.3 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.9.4 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.9.5 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.10 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.11 Important Facts:
- 1.12 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.13 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.14 Additional Facts:
- 1.15 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.16 Read More:
- 1.17 Leveraging Blockchain for Secure and Transparent Digital Identity Management
- 1.18 Share this:
- 1.19 Like this:
Why Mus you Read This Article?
Why should people read about Leveraging Blockchain for Secure and Transparent Digital Identity Management? Yes, I will tell you now that people should read about leveraging blockchain for secure and transparent digital identity management for several reasons:
Enhanced Security:
Blockchain technology provides a high level of security by utilizing cryptographic algorithms and decentralization. By storing digital identities on a blockchain, the risk of data breaches and identity theft can be significantly reduced. This can help individuals and organizations protect their sensitive information and maintain control over their identities.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Improved Privacy:
Traditional identity management systems often require individuals to share their personal information with multiple parties, leading to privacy concerns. Blockchain-based identity management allows individuals to have more control over their personal data. They can choose what information to share, with whom, and for how long, maintaining their privacy while still participating in digital transactions and interactions.
Transparency and Trust:
Blockchain’s transparent nature enables individuals and entities to verify and validate identities and transactions in a decentralized manner. This can help build trust among different parties, eliminating the need for intermediaries and reducing the potential for fraud. With transparent digital identity management, individuals can have more confidence in the authenticity and integrity of the identities they interact with.
Simplified Identity Verification:
Managing multiple usernames, passwords, and identity credentials across various platforms can be cumbersome. Blockchain-based identity management can simplify this process by creating a single digital identity that can be used across different services and platforms. This eliminates the need for remembering multiple credentials and streamlines the identity verification process for individuals.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Potential for Self-Sovereign Identity:
Blockchain technology has the potential to enable self-sovereign identity, where individuals have full control over their identities without relying on centralized authorities. With self-sovereign identity, individuals can manage and authenticate their own digital identities, reducing dependence on third parties and giving individuals greater autonomy over their personal information.
So, as you can see, by reading about leveraging blockchain for secure and transparent digital identity management, individuals can stay informed about the latest advancements in identity management technology. This knowledge can empower them to make informed decisions about their digital identities, protect their privacy, and participate in secure digital interactions.

Leveraging Blockchain for Secure and Transparent Digital Identity Management
Here are certain essential issues that explain what it means Leveraging Blockchain for Secure and Transparent Digital Identity Management. Just read them for a better understanding of the subject matter.
- How is blockchain used in digital identity management?
- What is blockchain for digital identity and security?
- What is leveraging blockchain technology?
Blockchain technology is used in digital identity management to provide secure and decentralized storage of identity information. Here’s how it works:
Immutable Records:
Blockchain ensures that once identity information is recorded on the blockchain, it cannot be tampered with or modified. Each identity record is stored in a block, linked to previous blocks through cryptographic hashes, creating a chain of information that is resistant to alteration.
Decentralization:
Traditional identity systems often rely on centralized authorities to manage and verify identities. In a blockchain-based identity system, identity verification can be decentralized, removing the need for a single authority. This allows individuals to have greater control over their own identity information.
Privacy Protection: Blockchain-based identity systems can provide users with control over their personal data. Users can selectively share specific identity attributes without revealing their entire identity. This enhances privacy and reduces the risk of identity theft.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Trust and Security:
Blockchain’s decentralized nature, combined with its cryptographic algorithms, provides a high level of security. Identity information is stored across multiple nodes in the network, making it difficult for attackers to compromise the system. Additionally, the use of public-private key cryptography ensures that only authorized individuals can access and update the identity records.
Leveraging blockchain technology refers to utilizing its unique features and capabilities to enhance various applications and systems. In the context of digital identity and security, leveraging blockchain means using its decentralized, transparent, and immutable nature to improve the management and verification of identities. By leveraging blockchain, organizations can create more secure, private, and user-centric identity systems that reduce reliance on central authorities and increase trust among participants.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Further Facts:
I understand that you need to know more about Leveraging Blockchain for Secure and Transparent Digital Identity Management. So, read on here.
- How can blockchain be used to improve security?
- blockchain-based personal identity security system
- concepts of identity in blockchain
Blockchain can improve security in several ways:
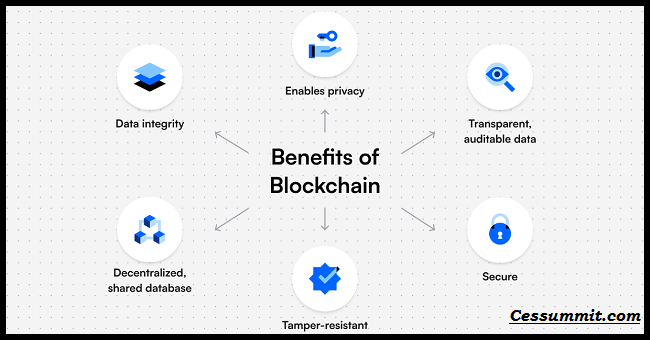
Data Integrity:
Blockchain’s distributed ledger technology ensures the integrity of data. Once information is recorded on the blockchain, it becomes tamper-proof and resistant to unauthorized modifications. This feature makes blockchain ideal for storing critical information, such as transaction records or sensitive data.
Immutability:
Once a transaction or data is recorded on the blockchain, it cannot be altered retroactively without consensus from the network participants. This immutability provides a high level of assurance and prevents malicious actors from manipulating or falsifying data.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Decentralization:
Traditional systems often rely on central authorities or intermediaries for verification and authorization, making them vulnerable to single points of failure or attacks. In a blockchain-based system, transactions and data are verified by a decentralized network of nodes, eliminating the need for a single authority and making it more difficult for attackers to compromise the system.
Consensus Mechanisms:
Blockchain networks use consensus mechanisms, such as Proof of Work (PoW) or Proof of Stake (PoS), to validate transactions and ensure agreement among participants. These mechanisms provide security by requiring network participants to invest resources or stake tokens, making it economically unfeasible for malicious actors to manipulate the system.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
When it comes to personal identity security, a blockchain-based system can enhance security and privacy by:
Self-Sovereign Identity:
Blockchain allows individuals to have greater control over their personal data. With a self-sovereign identity system, individuals own and manage their identity information, selectively sharing it as needed without relying on centralized authorities. This gives individuals more control and reduces the risk of identity theft.
Identity Verification:
Blockchain can enable more efficient and secure identity verification processes. Instead of relying on physical documents or third-party verifiers, blockchain-based identity systems can use cryptographic proofs and attestations to verify identities. This reduces the reliance on trusted intermediaries and minimizes the risk of identity fraud.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Secure Authentication:
Blockchain can provide a secure authentication mechanism for individuals. By using public-private key cryptography, individuals can prove their identity and authenticate themselves without revealing sensitive information. This enhances security while ensuring privacy.
Auditability:
The transparency of blockchain allows for enhanced auditability of identity-related activities. Transactions and changes to identity records can be traced and audited, providing a transparent and accountable system.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
In terms of identity concepts in blockchain, some key concepts include:
Identity Ownership:
Individuals have ownership and control over their own identity information. They can manage and share their identity attributes as per their preferences and consent.
Decentralized Identity:
Identity information is not stored in a central repository but is distributed across the blockchain network. This decentralization reduces the reliance on centralized authorities and enhances security and privacy.
Digital Signatures:
Digital signatures based on public-private key cryptography are used to authenticate and verify identities on the blockchain. These signatures ensure the integrity and authenticity of transactions and identity-related activities.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Identity Attestations:
Blockchain allows for the creation of identity attestations, which are claims or assertions about an individual’s identity. These attestations can be made by trusted parties or entities and are stored on the blockchain, providing verifiable proof of identity.
Interoperability:
Blockchain-based identity systems aim to be interoperable, allowing individuals to use their digital identities across various applications and platforms without the need for multiple identity providers. This improves user experience and reduces the need to share redundant identity information.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Important Facts:
- digital identity crypto projects
- how to use blockchain to verify identity
- distributed identity blockchain
There are several crypto projects focused on digital identity. Here are a few notable examples:
Sovrin (Sovrin Foundation):
Sovrin is a decentralized identity network built on blockchain technology. It aims to provide individuals with control over their digital identities and enable secure and privacy-preserving identity verification.
uPort (Consensys):
uPort is a self-sovereign identity platform that allows users to create, manage, and control their identities on the blockchain. It enables selective disclosure of identity attributes and offers secure authentication using blockchain-based credentials.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Civic (Civic Technologies):
Civic is a blockchain-based identity verification platform that allows individuals to securely store and share their identity information. It utilizes blockchain technology to verify and authenticate identities in a decentralized manner.
SelfKey (SelfKey Foundation):
SelfKey is a blockchain-based self-sovereign identity system that provides individuals with full control over their identity data. It offers a marketplace where users can manage their identity documents and perform identity verification processes.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Using blockchain to verify identity involves the following steps:
Creation of Digital Identity:
A user creates a digital identity by generating a public-private key pair. The private key is securely stored by the user, while the public key becomes part of their digital identity.
Identity Verification: To verify the identity, the user provides relevant identity information and supporting documents. This information can be verified by trusted third-party entities or attestors, such as government agencies or financial institutions.
Attestation and Recording:
The verified identity information is then attested by the verifying parties. These attestations serve as proofs or assertions about the user’s identity. The attested information, along with the user’s public key, is recorded on the blockchain.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Authentication and Access:
When the user needs to authenticate themselves or access a service, they can use their private key to sign a digital transaction or provide cryptographic proof of identity. The service provider or verifier can then verify the user’s identity by validating the digital signature or proof against the recorded identity information on the blockchain.
Distributed identity on the blockchain refers to the concept of decentralizing identity management. Instead of relying on a central authority or identity provider, identity information is distributed across the blockchain network. This distribution ensures that no single entity has full control over users’ identities, enhancing security and privacy. Distributed identity systems leverage blockchain’s features such as immutability, transparency, and decentralization to enable individuals to have greater ownership and control over their digital identities.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Additional Facts:
Here too are additional facts on Leveraging Blockchain for Secure and Transparent Digital Identity Management. It;s important you read them.
- centralized vs decentralized identity management
- blockchain idm
- decentralized identity crypto
Centralized Identity Management:
In a centralized identity management system, a central authority or organization controls and manages the identity information of individuals. This central authority acts as the trusted party responsible for verifying and authenticating identities. Users rely on this authority to store and manage their identity data and to access services that require identity verification. However, this approach has some drawbacks, including:
Single Point of Failure: A centralized authority becomes a single point of failure. If the central authority’s systems are compromised, it could result in a significant data breach or identity theft.
Lack of User Control: Users have limited control over their own identity data. They must rely on the central authority to manage and protect their information, raising concerns about privacy and data security.
Data Silos: Each centralized authority typically maintains its own database of identities. This can lead to fragmented and duplicated identity information across different services and organizations, causing inefficiencies and hindering interoperability.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Decentralized Identity Management:
Decentralized identity management, also known as self-sovereign identity, shifts the control and ownership of identity information to individuals themselves. It leverages decentralized technologies, such as blockchain, to provide a more secure, user-centric, and privacy-preserving approach. Key aspects of decentralized identity management include:
User Ownership and Control: Individuals have ownership and control over their identity information. They can create and manage their digital identities, selectively disclose attributes, and authenticate themselves without relying on a central authority.
Privacy and Security: Decentralized identity solutions prioritize privacy and security. Personal data is stored locally or in secure digital wallets, and individuals can choose which attributes to share with different entities, reducing the risk of data breaches and identity theft.
Interoperability: Decentralized identity systems aim to establish interoperability standards, enabling users to seamlessly use their digital identities across various applications, platforms, and services. This eliminates the need to create and manage multiple identities for different services.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Blockchain for Identity Management:
Blockchain technology can be leveraged to facilitate decentralized identity management. Blockchain provides the following benefits for identity management:
Data Integrity and Immutability: Blockchain’s tamper-proof and immutable nature ensures that once identity data is recorded, it cannot be altered or modified without consensus from the network participants. This enhances the trustworthiness of identity information.
Decentralization: Blockchain-based identity management distributes identity information across a network of nodes, removing the need for a central authority. This enhances security by eliminating single points of failure and reducing the risk of data breaches.
Trust and Transparency: The transparency of blockchain allows for increased trust in identity verification processes. Transactions and changes to identity records are transparent and auditable, providing a higher level of accountability.
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Decentralized Identity Crypto:
Decentralized identity crypto refers to cryptocurrencies or tokens that are specifically designed to support decentralized identity systems. These tokens can be used for identity verification and authentication, and to establish trust in the decentralized identity ecosystem. They may serve as a means of attestation, reputation, or as a utility within decentralized identity networks. These tokens are typically built on blockchain platforms and follow relevant standards and protocols, such as the Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) specifications.

Leveraging Blockchain for Secure and Transparent Digital Identity Management
Read More:
- The Role of Blockchain Technology in Cryptocurrency
- The Potential Benefits of Adopting E-Naira in Business Operations
- The Role of E-Naira in Fostering Financial Inclusion for Business Owners
- E-Naira and Digital Marketing in Nigeria
- How to Harness The Power of E-Naira for Cashless Payments in Business
- How to Write Winning Proposals that Close Deals
- How to Raise Funds for Your Project by Crowdfunding
- Cessummit.com Services Offerings: What we do & How
- Profitable Business Idea
Leveraging Blockchain for Secure and Transparent Digital Identity Management
Now, we are concluding; the adoption of blockchain technology for secure and transparent digital identity management holds immense potential to revolutionize how we handle identity verification and data privacy. By utilizing decentralized networks, cryptographic protocols, and smart contracts, blockchain ensures that personal information is protected, tamper-proof, and accessible only to authorized parties. With enhanced security and transparency, individuals gain control over their digital identities, reducing the risk of identity theft, fraud, and data breaches.
Moreover, blockchain-based identity management systems can streamline processes, reduce administrative costs, and improve efficiency across various sectors, such as finance, healthcare, and government. As we continue to explore and refine the implementation of blockchain solutions, we move closer to a future where individuals have greater trust and confidence in digital interactions, unlocking a wide range of opportunities for innovation and empowerment.